Hedgey Finance Exploit: Six Months Later, Lessons Learned, and Code Revamped
On April 19, 2024, Hedgey Finance faced an exploit resulting in the loss of approximately $2 million on the Ethereum network, along with numerous BONUS tokens on the Arbitrum network.
This breach, due to a vulnerability in the ClaimCampaigns.sol contract, highlighted the critical role of smart contract security and the need for contract audits of high-value audits.
This article revisits the incident 6 months later, analyzes the attack flow, and examines Hedgey Finance’s response and the ongoing impact. We will also see the modifications made to the claim functionality.
Key Vulnerability and Attack Flow
Vulnerable Contract: ClaimCampaigns.sol
- Contract Address: 0xBc452fdC8F851d7c5B72e1Fe74DFB63bb793D511
- Exploit Overview: The attacker exploited the createLockedCampaign() function, which lacked a mechanism to revoke token approvals after campaign cancellation. Consequently, the attacker could transfer funds by leveraging the transferFrom function, due to lingering token approvals.
Detailed Attack Flow
- Initiation: The attacker initiated a flash loan of 1.305 million USDC from Balancer as shown in the transaction flow below.
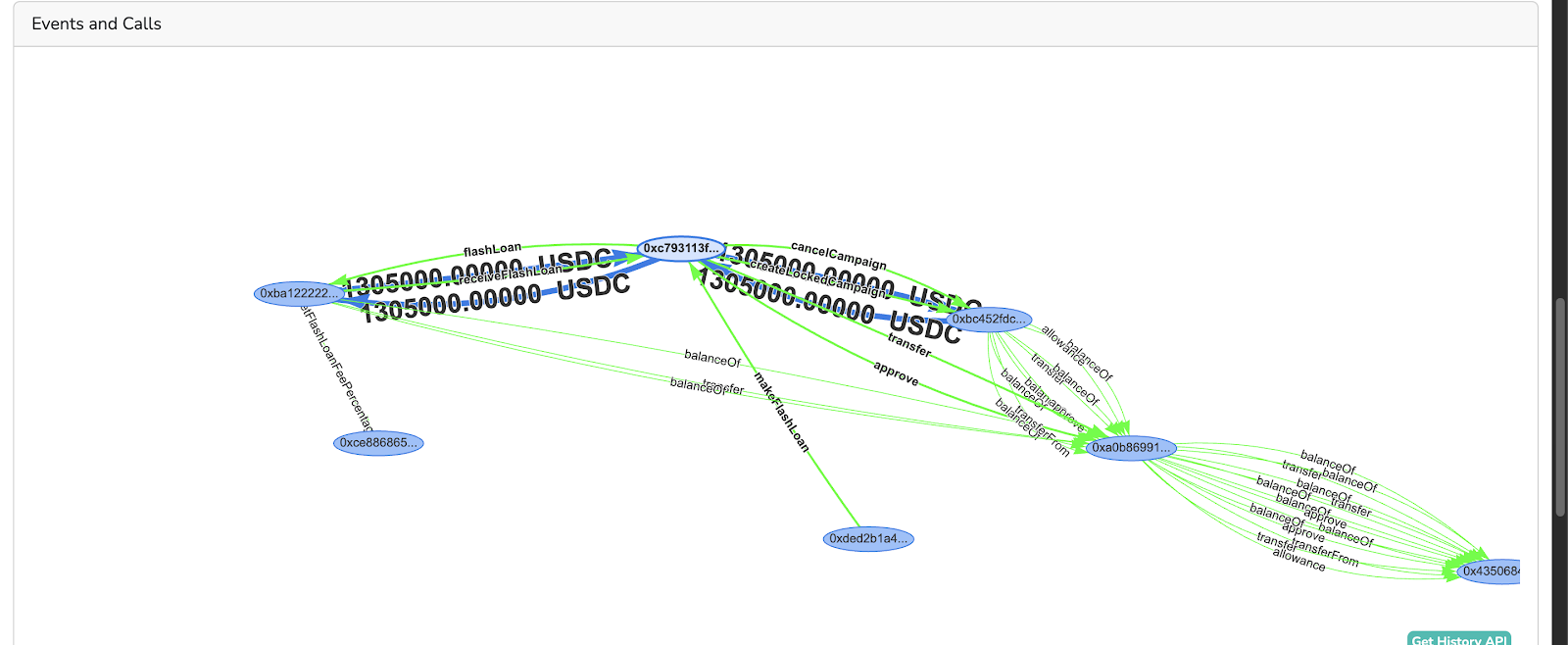
- Approval Exploit: The attacker called the createLockedCampaign() function, granting themselves an approval to transfer USDC tokens.
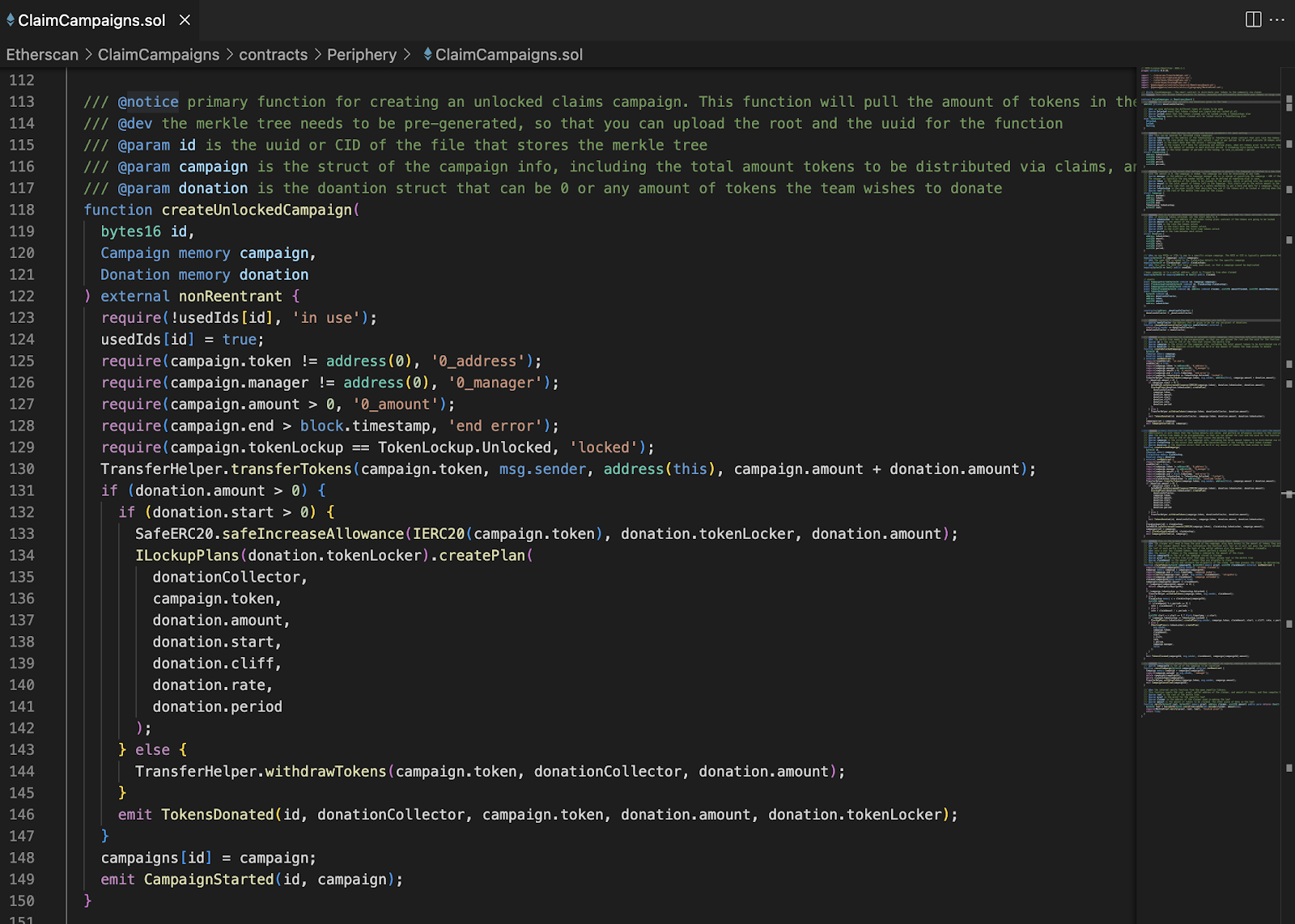
We don’t see this function now in the ClaimCampaigns.sol file which is now replaced with createUnlockedCampaign()
-
Cancellation with Exploit:
-
Within the same transaction, they called cancelCampaign(), withdrawing USDC without revoking the approval.
-
Execution of Transfer:
-
In a follow-up transaction, they used transferFrom() to move 1,303,910 USDC out of the Hedgey Finance account.
- Repeat Exploit: The attacker repeated the process with BONUS tokens on Arbitrum, resulting in an additional loss of approximately $600,000.
Visualizing the Attack Flow
Here’s a simplified flowchart detailing the exploitation process:
Each of these steps involved manipulating the createLockedCampaign() and cancelCampaign() functions to gain control over Hedgey Finance’s assets.
Impact Breakdown
- Total Loss: $2 million USD in various tokens, with the largest single extraction at 1.3 million USDC.
- Additional Losses: Approximately $20,000 in MASA tokens and 78,148,820 BONUS tokens taken through similar exploits by copycat attackers.
- Identified Attackers: At least three attackers were involved, with one primary address executing most of the losses on Ethereum.
Timeline of Key Events
- April 19, 2024: Initial exploit occurs; Hedgey loses $2 million.
- April 20, 2024 - Present: Hedgey Finance collaborates with cybersecurity firms to investigate and recover funds.
- Post-April 2024: Additional minor exploits by copycat attackers take a further $20,000 and 78 million BONUS tokens.
Hedgey Finance’s Response
-
Immediate Communication: - Lindsey Winder of Hedgey Finance swiftly addressed the community on social media, pledging action and transparency.
-
Investigation and Collaboration: - Partnered with cybersecurity firms, law enforcement, and impacted entities to track and recover funds. Hedgey Finance kept users informed through regular updates.
-
Security Enhancements: - Conducted multiple audits and implemented security improvements to prevent similar incidents. - Introduced white hat bounties to encourage vulnerability identification. - Developed Hedgey 2.0 with more robust security.
-
Community Support: - Supported impacted users by collaborating on token claim pages and providing regular updates, particularly to the NobleBlocks community.
Impact on Redeem and Plan Creation Rates
Redeem Activity Analysis
- Pre-Hack (April 1 - April 18): Average of 19.43 redeem plans per day.
- Post-Hack (April 19 onward): Average dropped to 7.62 redeems per day.
- Observation: The decline suggests a decrease in user confidence initially, though total post-hack redeems show a rebound over time.
Plan Creation Analysis
- Pre-Hack (April 1 - April 18): Average of 31.41 plans created per day.
- Post-Hack: Decreased slightly to 27.16 plans per day.
- Observation: While a drop is observed, total post-hack plan creation saw a recovery, indicating regained user confidence.
Code Fix and Updated cancelCampaign() Function
Hedgey Finance updated the cancelCampaign() function to prevent unauthorized token transfers after campaign cancellation. The updated code snippet now deletes campaign approvals and lockups before initiating the token transfer, ensuring any unclaimed tokens are returned to the campaign manager without leaving approvals vulnerable.
Long-Term Effects and Community Sentiment
-
Reputation Impact: - Hedgey Finance’s reputation suffered initially, but transparency in communication and a proactive response helped mitigate damage.
-
User Trust and Activity: - User trust took a hit, as evidenced by reduced platform engagement in the immediate aftermath. However, Hedgey’s efforts to support affected users and enhance platform security gradually restored confidence.
Lessons Learned and Preventive Measures
Key Recommendations for DeFi Developers
- Revoke Approvals: Always revoke token approvals in contracts once they are no longer needed.
- Use Secure ERC20 Implementations: Secure implementations from trusted sources like OpenZeppelin are essential.
- Multi-Sig Wallets: Implement multi-signature wallets for sensitive transactions to prevent unauthorized access.
- Audits and Testing: Comprehensive audits and rigorous testing can identify and mitigate vulnerabilities before deployment.
User Education
- Users should regularly review and revoke token permissions, avoid unaudited projects, and consider hardware wallets for additional security.
Conclusion
The Hedgey Finance exploit underscored the necessity of thorough security protocols in DeFi platforms. Hedgey’s swift response, including increased security measures, transparent communication, and community engagement, has fostered a sense of renewed confidence. This incident serves as a critical reminder for all stakeholders in the DeFi ecosystem about the importance of continuous auditing, user education, and proactive vulnerability management.